AI-Powered Chatbot for Healthcare Provider 3
Automated patient support with a secure, intelligent chatbot for clinics and hospitals.
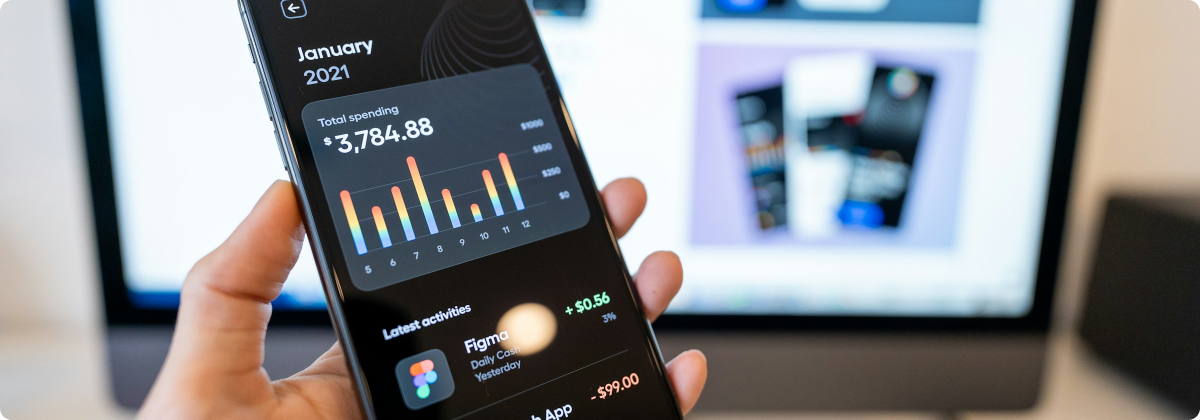
We offer complete mobile app development services, covering everything from idea creation to secure, user-friendly deployment.
Don’t Worry, Here Is Your Answer! We make your app faster by improving performance and more secure with strong protection measures.
We update old systems with scalable, future-proof solutions that improve efficiency, compatibility, and long-term business success.
Our team applies strong security measures and ensures your systems comply with the latest industry regulations.
We link disconnected systems using APIs and middleware, ensuring smooth and consistent data sharing across all platforms.
Using agile development, we help launch products faster, giving your business an edge in the market.
Our experts enhance your infrastructure to improve speed, reliability, and scalability, ensuring peak performance at all times.
We improve your existing systems, creating solutions that boost returns and increase operational efficiency across your business.
We integrate advanced cybersecurity measures into every layer of your AI-based software to safeguard your data and ensure secure operations.
We conduct rigorous penetration testing to identify and fix vulnerabilities, ensuring the app is secure before deployment.
We integrate robust authentication mechanisms, such as biometrics, two-factor authentication, and OAuth, to prevent unauthorized app access.
Our apps are built with tools to detect and mitigate malware, protecting users from potential security threats.
We provide regular security patches and updates to address vulnerabilities and keep your app resilient against evolving threats.
We serve a wide range of industries, providing mobile app solutions that meet the unique needs of each sector.
We create mobile apps that enhance the shopping experience, improve customer engagement, and streamline transactions.
Enhanced Shopping Experience
We develop interactive learning apps, online courses, and educational tools to improve the learning experience.
Interactive Learning Tools
We offer secure mobile solutions for online banking, payment processing, and financial tracking.
Secure Financial Solutions
We build mobile apps for property listings, virtual tours, and easy communication between buyers and agents.
Seamless Property Management

Our expertise in modern technology ensures your mobile app is built to perform and protect.
